Moectf 2023 Re-Writeup
base_64
uncompyle6反编译pyc
1 | # uncompyle6 version 3.9.0 |
enc_flag经过str.maketrans方法处理,将string2表中的字母替换成了string1表内的,两个交换一下还原出flag的密文再base64解码一下即可。
moectf{pYc_And_Base64~}
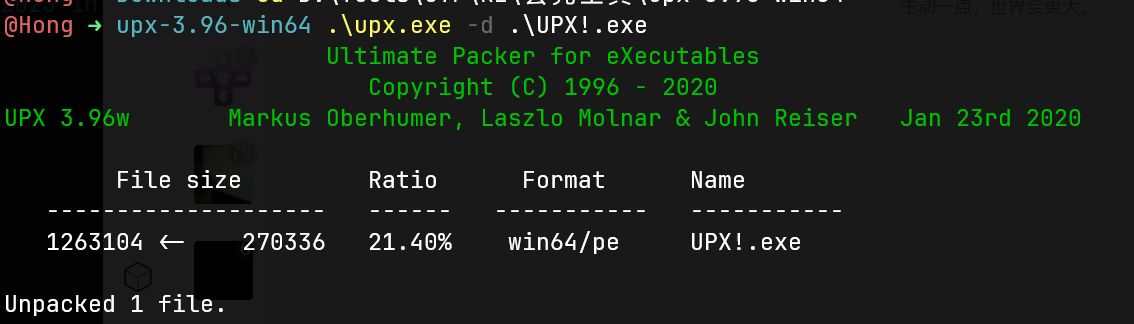
UPX!
peid看到加了upx的壳,upx脱下壳就行。
核心代码
1 | for ( j = 0; ; ++j ) |
考点还是异或,没啥说的。
1 |
|
moectf{0h_y0u_Kn0w_H0w_to_Rev3rse_UPX!!!}
Xor
核心代码
1 | gets(input); |
输入的flag与0x39异或得到密文,再异或个0x39就能还原出flag。
1 | enc = [ |
moectf{You_kn0w_h0w_t0_X0R!}
ANDROID
核心代码
1 | public class MainActivity extends AppCompatActivity { |
这段代码定义了一个加密字符串(enc)和一个密钥(key),然后在 onCreate() 方法中检查文本框中输入的异或处理过的字符串是否与加密字符串匹配。
核心代码即v7_1[v0] ^ MainActivity.this.key[v0 % MainActivity.this.key.length]) != MainActivity.this.enc[v0]
1 | enc = ['\u0019', '\u0007', '\u0000', '\u000E', '\u001B', '\u0003', '\u0010', '/', '\u0018', '\u0002', '\t', ':', '\u0004', '\u0001', ':', '*', '\u000B', '\u001D', '\u0006', '\u0007', '\f', '\t', '0', 'T', '\u0018', ':', '\u001C', '\u0015', '\u001B', '\u001C', '\u0010'] |
moectf{Java_in_Android_1s_easy}
EQUATION
All articles in this blog are licensed under CC BY-NC-SA 4.0 unless stating additionally.
